Given the array of options out there, choosing the proper non-custodial crypto wallet tailored to your preferences can be difficult. Nonetheless, sure elements must be taken into consideration before making a decision based on your experience degree and particular requirements. Integrate crypto wallets, IBAN accounts, and seamless funds into your small business operations.
- It provides offline backup options, enabling users to immediately entry and recover their assets.
- A crypto wallet is a digital or software-based method to entry your cryptocurrencies.
- While your non-public keys can’t be revealed whereas you’re offline, the tradeoff for this further security is much less comfort.
- Some in style examples of non-custodial wallets are hardware wallets like CoolWallet, NGRAVE and Ledger.
- Before you select a self-custody pockets, you should know the differing types.
Hierarchical Deterministic (hd) Wallets
Elliptic Curve Digital Signature Algorithm (ECDSA) is one such signature scheme that does so. If a nonce is reused with ECDSA, it might possibly result in key compromise. Numerous different algorithms aren’t affected so, as usual, ensure well-established cryptographic libraries are being used.
Non-custodial Vs Custodial Wallets
This can be especially necessary for anyone wishing to retailer massive quantities of crypto on trade accounts. Having full ownership of their own cryptocurrency can make them really feel extra comfy when using your platform. Crypto addresses (and their private keys) are automatically created whenever you arrange a crypto pockets.
It provides intensive assist for varied cash and tokens and operates on an open-source platform fostering community-driven progress. This makes them best for frequent transactions but in addition more exposed to hacking attempts. To mix the security of a hardware pockets with the functionality of your Crypto.com account, you probably can pair your Trezor or Ledger by way of an extension pockets. Beneath are probably the most suitable pockets options for companies—not consumers—based on security, compliance, workflow automation, and integration potential. Every deposit and withdrawal is visible on public blockchains, supporting audits and monetary oversight. Since custodial wallet suppliers are usually centralized, they’ve extra regulations to abide by corresponding to KYC (Know Your Customer) and AML (Anti-money Laundering).
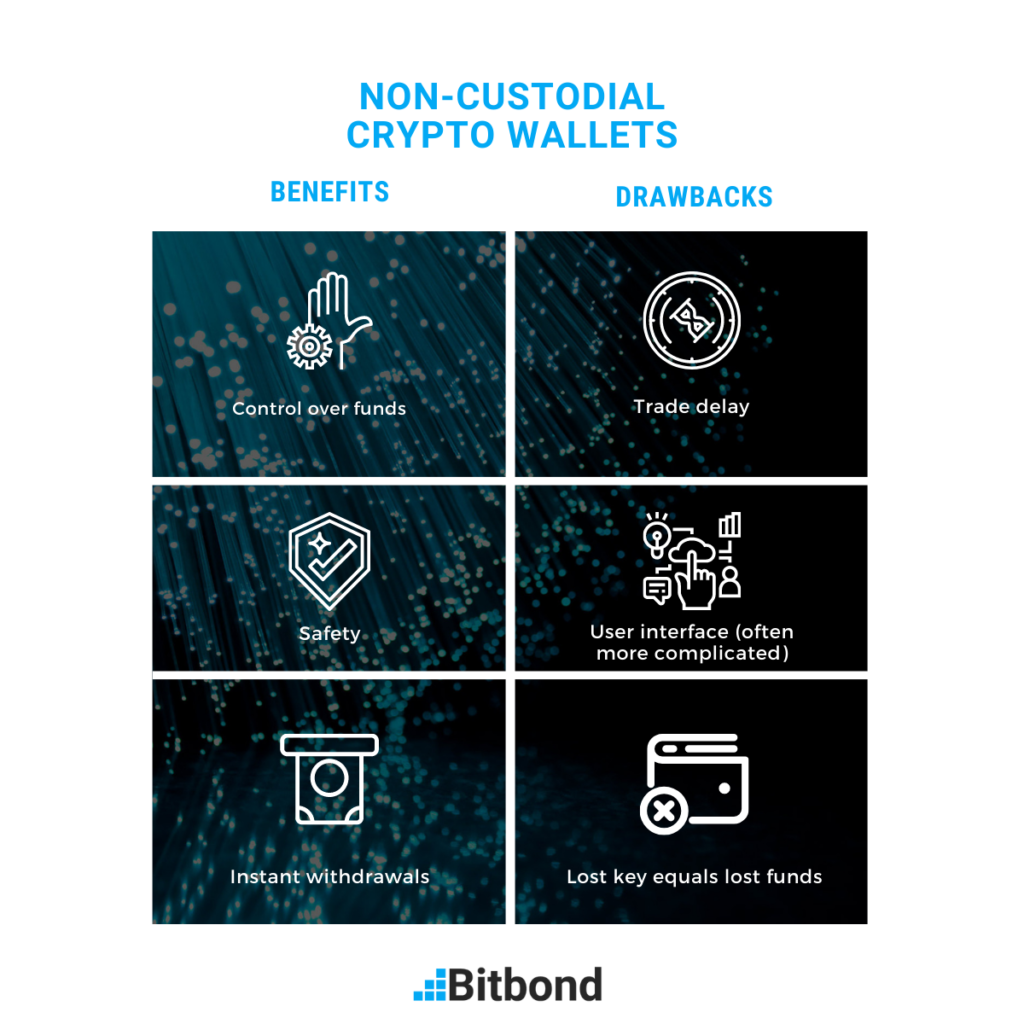
In this post, we focus on Crypto Wallet for Brokers: Main Reasons to Use It the top non-custodial wallets of 2023, including information about their unique makes use of and characteristics. Whether you require secure storage for a specific cryptocurrency or need a feature-rich pockets for engaging with DeFi dApps, this article will let you know every thing you should know. With a non-custodial pockets, only you maintain the keys, and only you can authorize transactions.
Faq About Crypto Wallets
The question of custodial or non-custodial is targeted on who’s responsible for the safety of the vital thing administration. Privy enables you to layer on defenses like passkey signing, pockets policies, transaction MFA, multisigs and more to create layers of safety for your customers and their funds. Privy powers hardware-secured, SOC 2‑compliant wallets for any user—across EVM, Solana, Bitcoin, and extra.
As the sole authority, if a person loses their hardware wallet or forgets their pin or password, they could lose access to their funds eternally. Moreover, some non-custodial wallets (such as hardware wallets) keep the personal key offline, additional enhancing safety by decreasing publicity to on-line threats. These are types of wallets the place the crypto exchange holds half of the private keys while the other half is with the end consumer.

Which Is The Most Secure Crypto Wallet?
The commonest safeguards listed right here are PIN codes or passphrases. As at all times, these should be sufficiently lengthy and complicated – utilizing many several types of characters – to be maximally effective. More superior forms of authentication can embrace biometrics or public key encryption-based approvals, such as cryptographic signatures from multiple other secured devices.
